Android and the mysteries of dial codes – Extracting dial codes by apk reversing
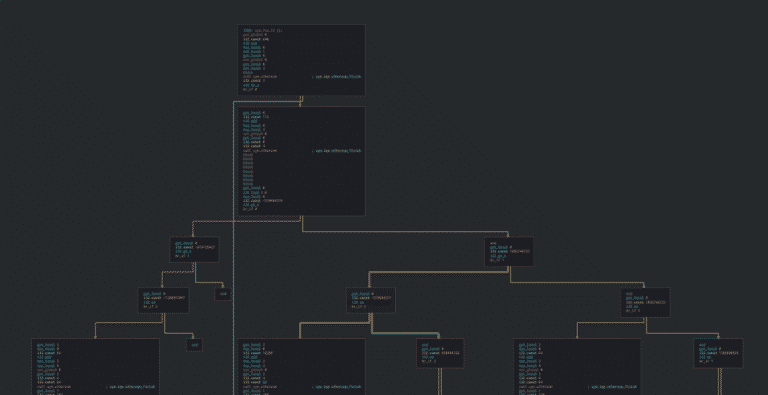
Android and the mysteries of dial Codes Extracting dial codes by apk reversing Dial Codes, also called USSD or HMI (Human Machine Interface) codes, are typically used by OEM and carrier to implement some menu. While making baseband researches, those hidden menus was very useful. Today, in this small blogpost, I will described the way…