Benchmarking LLMs agents for vulnerability research
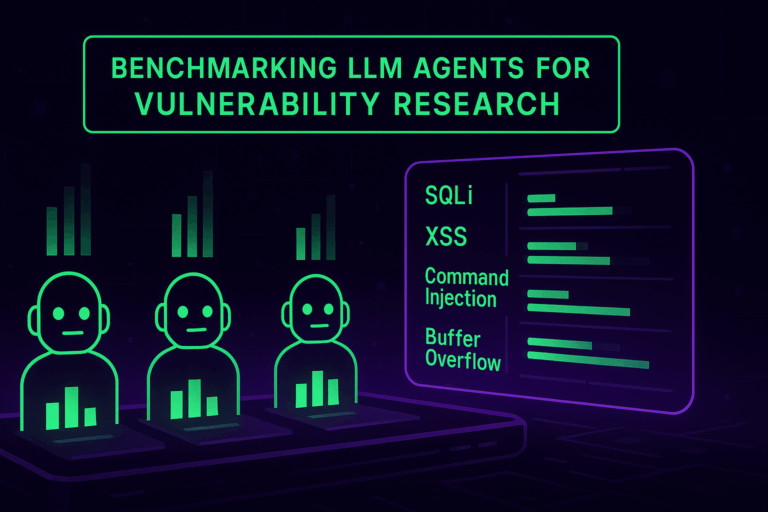
applied AI for Cybersecurity Benchmarking LLM agents for vulnerability research AI agents appear to be a powerful tool for advancing vulnerability research and securing modern applications. At FuzzingLabs, we decided to take a deep dive into this topic to assess its real-world potential. We conducted experiments by building AI agents using various LLMs, with the…