EVM Security
Insights from Zer0Con 2025
At Zer0Con 2025, the FuzzingLabs team, Mathieu Hoste and Bryton Bernard, delivered an engaging and insightful presentation on one of the most critical aspects of Ethereum’s security: the vulnerabilities within the Ethereum Virtual Machine (EVM). In our session, titled “Ethereum’s Achilles’ Heel: Attacking and Fuzzing EVMs for Fun (and Profits)” we demonstrated how fuzzing has been instrumental in uncovering severe flaws in various EVM implementations.

As the backbone of Ethereum’s decentralized applications (DApps), the EVM is responsible for executing smart contracts and transactions. However, due to its complex nature, the EVM is susceptible to security vulnerabilities that could pose significant risks to both smart contracts and the Ethereum network. We highlighted several critical vulnerabilities, ranging from memory corruption to gas miscalculations, all of which have the potential to destabilize the Ethereum ecosystem.
Multiple EVM Implementations: Opportunities and Risks
One of the major points we emphasized during our talk was the importance of having multiple EVM implementations. Implementations like Geth (Go Ethereum), Ethrex LEVM, and Substrate EVM enhance scalability, performance, and cross-chain interoperability. However, this variety also increases the attack surface—each implementation has unique vulnerabilities that could be overlooked if not thoroughly tested. We shared how our fuzzing efforts across different EVMs revealed serious issues that could compromise network security.
Fuzzing Strategies: Uncovering Hidden Threats
Our fuzzing strategies, which included both differential fuzzing and coverage-guided fuzzing, were showcased as highly effective tools for detecting inconsistencies and vulnerabilities across different EVM implementations. By feeding mutated bytecode into various EVMs and analyzing their behavior, we were able to uncover significant discrepancies in areas such as gas usage, stack manipulation, and memory access. For instance, our coverage-guided fuzzing of Aurora—a Rust-based EVM—exposed integer overflow vulnerabilities that could lead to node crashes. Similarly, we found issues with Ethrex LEVM’s transaction gas cost calculation, which didn’t align with Ethereum’s standard specifications.
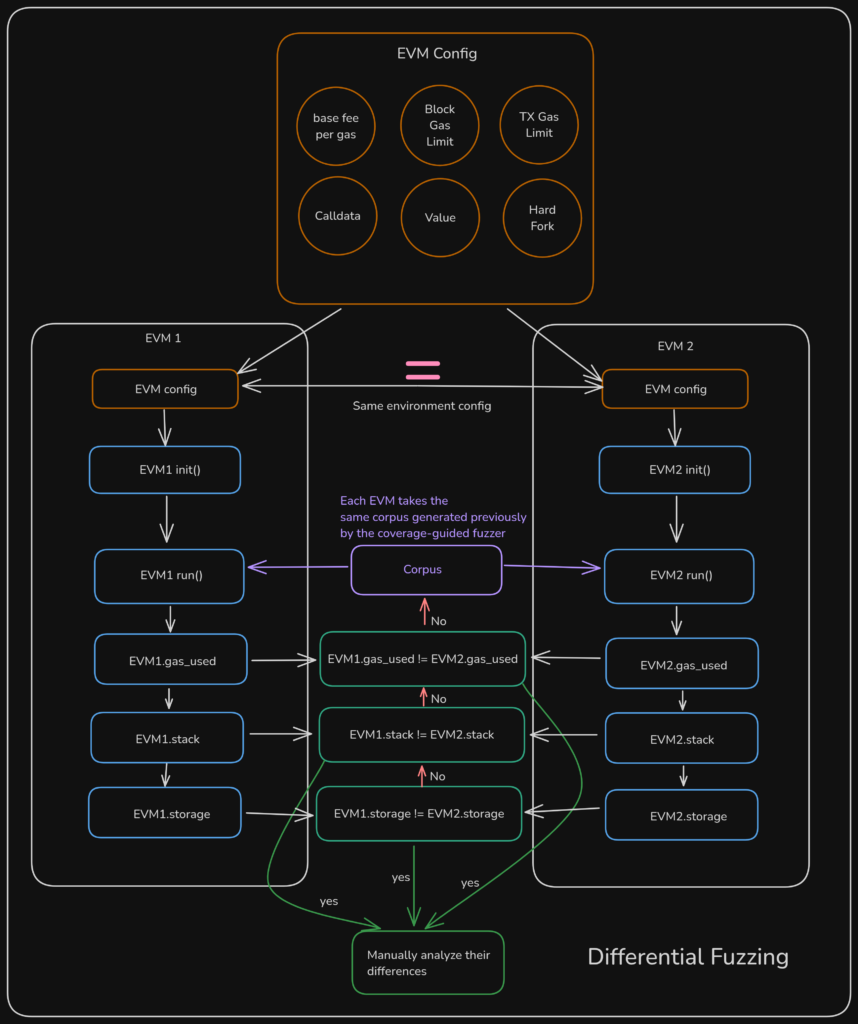
Differential fuzzing allowed us to compare EVM implementations against the expected behavior described in the Ethereum Yellow Paper, revealing subtle but critical differences that could lead to serious issues like broken execution proofs, failed indexers, and potential consensus failures.
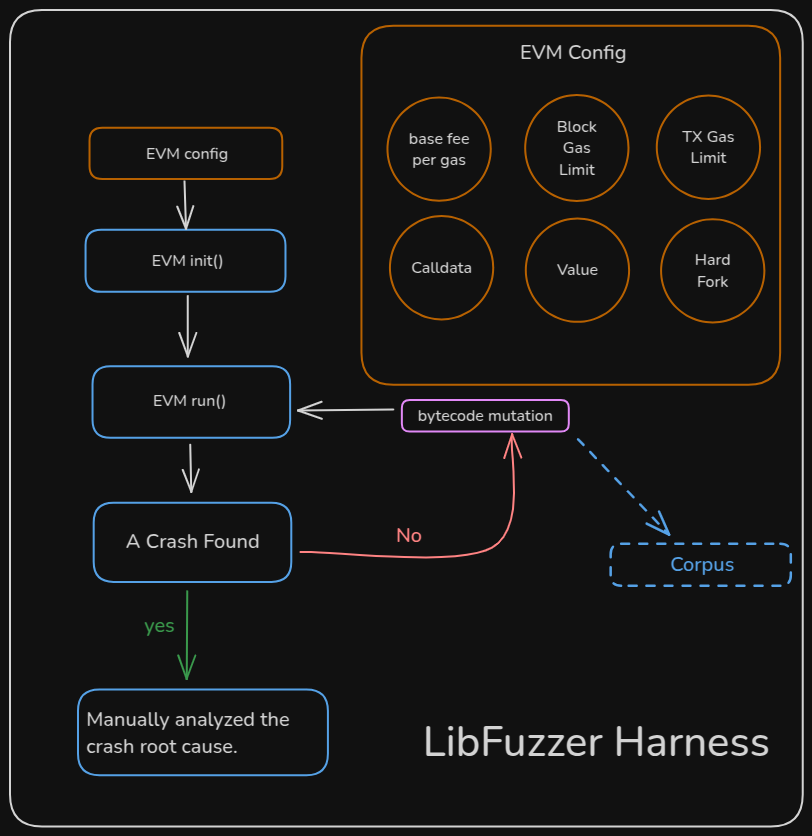
Meanwhile, our coverage-guided fuzzing focused on continuously mutating bytecode to explore different execution paths and trigger crashes. This approach helped identify more deeply embedded flaws, allowing us to pinpoint specific areas in the EVM code where failures occurred and assess their impact on overall security.
By using both techniques, we were able to uncover vulnerabilities that might have otherwise gone unnoticed, ensuring that EVM implementations are more resilient against potential attacks.
Fuzzing Strategies: Uncovering Hidden Threats
We concluded with a powerful statement: “Every EVM is a potential zero-day.” Our findings reinforced the idea that fuzzing is not just about finding bugs—it’s about pushing EVM implementations to their limits and identifying vulnerabilities that could lead to significant security risks. We highlighted the importance of continuous fuzz testing across all EVM implementations, especially as the Ethereum ecosystem continues to expand and new implementations emerge.
For us at FuzzingLabs, ensuring the security of the EVM is critical for the continued trust and integrity of the entire blockchain. Our research at ZeroCon 2025 served as a reminder to the development community that security must remain a top priority. By rigorously testing and hardening the EVM through fuzzing, we can ensure that Ethereum remains resilient to attacks and continues to thrive in an increasingly complex digital landscape.
Slides of the presentation can be found on our Github.
About Us
Founded in 2021 and headquartered in Paris, FuzzingLabs is a cybersecurity startup specializing in vulnerability research, fuzzing, and blockchain security. We combine cutting-edge research with hands-on expertise to secure some of the most critical components in the blockchain ecosystem.
Contact us for an audit or long term partnership!



