Practical Web Browser Fuzzing
Discover how to uncover browser vulnerabilities and automate bug discovery effortlessly!
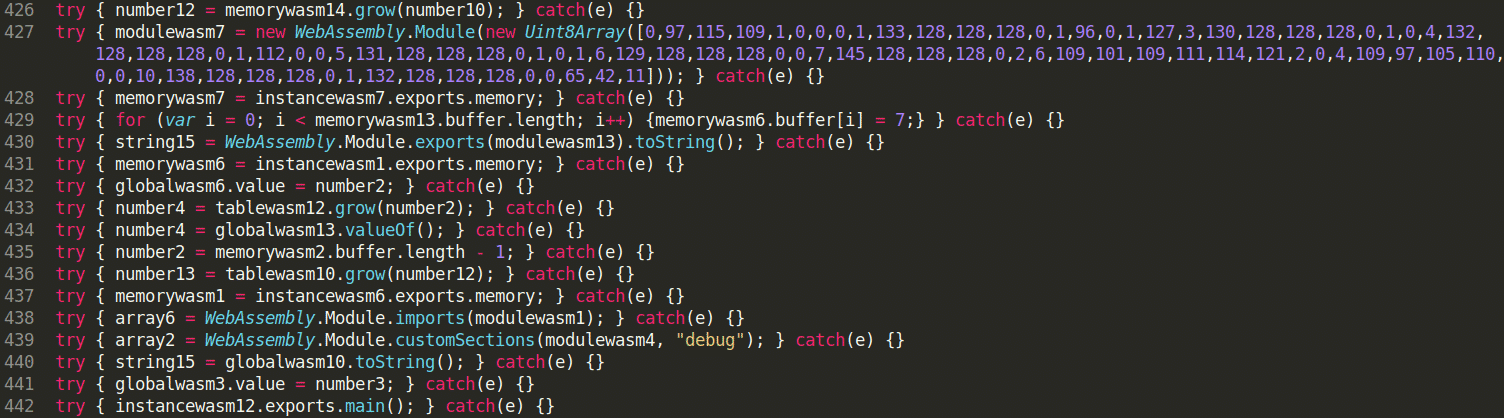
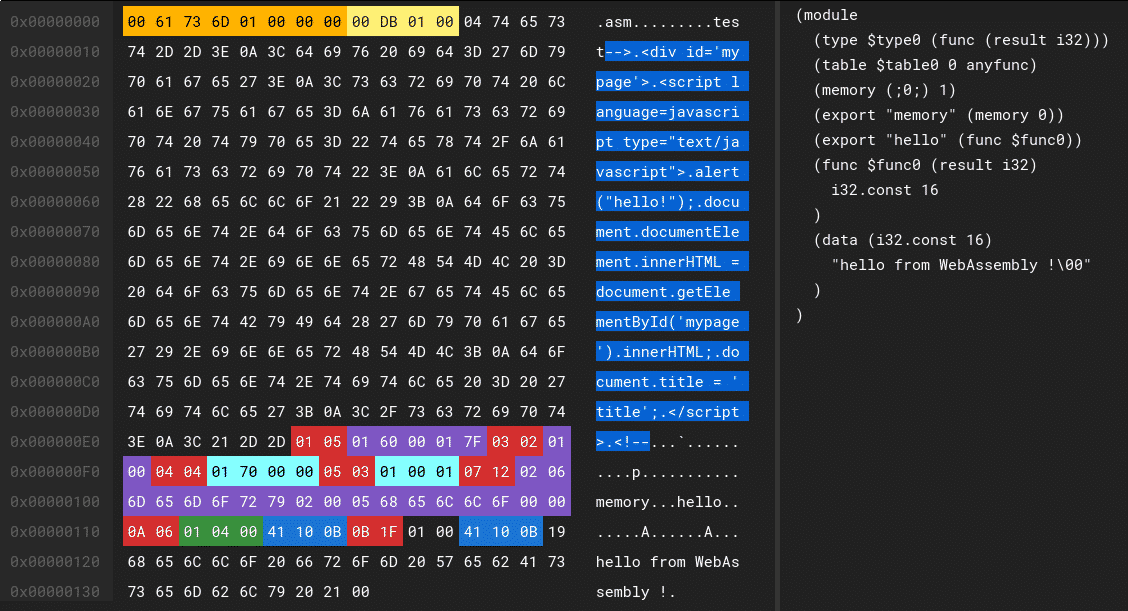
This hands-on training focuses on advanced techniques in web browser fuzzing, equipping you with the skills to detect browser-specific vulnerabilities, automate testing workflows, and analyze crash reports effectively. Learn to harness cutting-edge fuzzing tools and methodologies to stay at the forefront of browser security research.
⏳ 32 hours | 🧑🎓 100+ students | 🔄 Last updated: 15/01/2025