Introduction to KVM & Hardware Virtualization
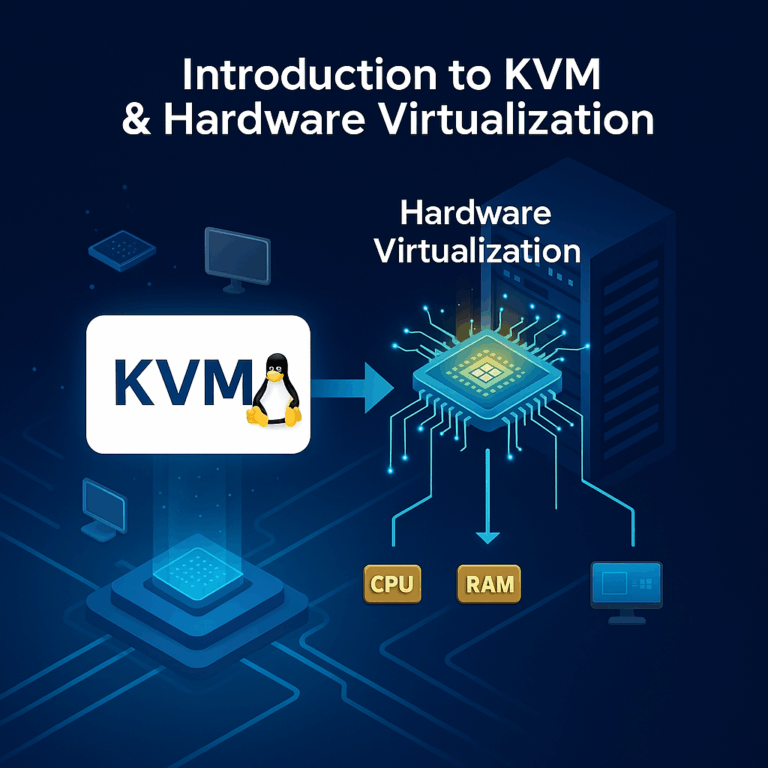
Hardware virtualization Introduction to KVM & Hardware Virtualization Virtualization has become a huge part in production environments, in traditional IT or in the cloud, improving security, development cycles and maintenance. This technology is the cornerstone that allows us to build isolated sandboxes, drastically shorten the time it takes to provision new servers, and perform hardware…