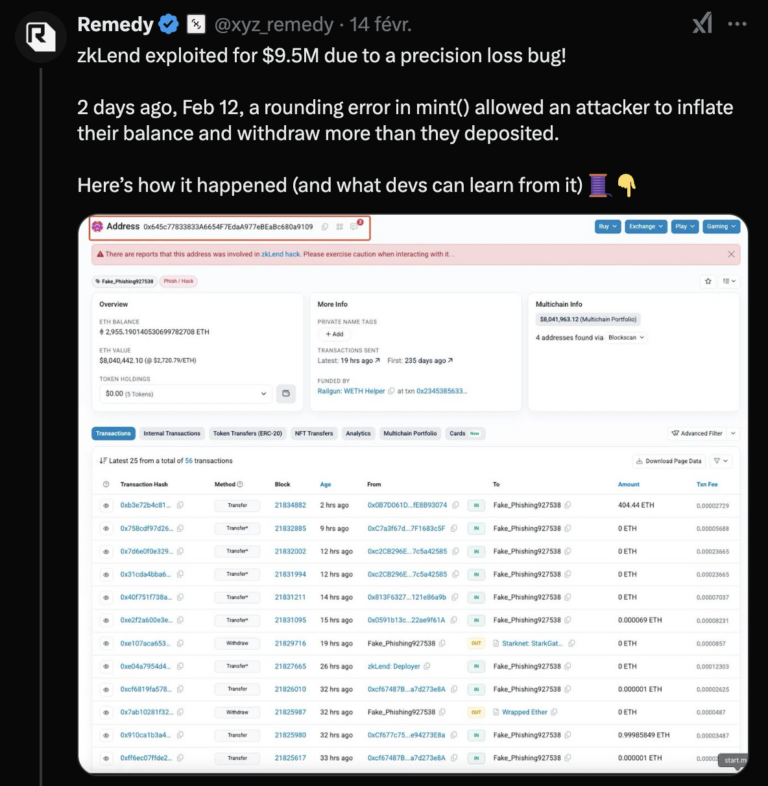
rediscovery of the starknet zklend hack
How Fuzzing Could Have Prevented the zkLend Hack
The recent zkLend hack has stirred up significant discussion in the community, and today we’d like to share some insights from our deep dive into the vulnerability using fuzzing techniques at FuzzingLabs. Our investigation reveals that a simple fuzzing test could have detected the flaw in a matter of seconds.
What Went Wrong?
At the heart of the vulnerability lies a function in zkLend’s core code—specifically, in the safe_decimal_math library. This function is used to perform a division operation safely by scaling decimals. The issue surfaces when this division is employed in the market deposit logic.
The problematic usage can be found in the z_token/external.cairo file, which in turn is called during a deposit on the market.
A closer look revealed that the division function could produce an unexpected result: the scaled down amount, calculated by dividing the amount by an accumulator, may end up larger than the original amount due to an issue with the underlying arithmetic breaking an important invariant.
Fuzzing to the Rescue
Our team created a simple fuzzing harness to reproduce the vulnerability. Here’s the key snippet used in our fuzz test:
#[starknet::contract]
mod FuzzMarketAccumulator {
use super::super as crate;
use crate::libraries::{safe_decimal_math};
#[storage]
struct Storage {}
#[external(v0)]
fn fuzz_scaled_down_amount(ref self: ContractState, amount: felt252, accumulator: felt252) {
let scaled_down_amount = safe_decimal_math::div(amount, accumulator);
assert(Into::<_, u256>::into(scaled_down_amount) <= Into::<_, u256>::into(amount), 0x15);
}
}
In this simple test, we divide amount by accumulator and assert that the resulting scaled_down_amount does not exceed the original amount. The violation of this invariant indicates the presence of the bug.
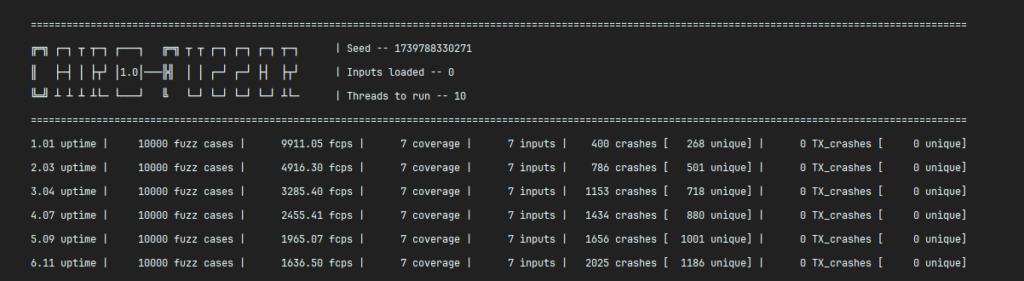
Using the cairo-native-fuzzer compiled in Sierra mode, our fuzz test identified the issue in just 1 second:
cargo run -- --sierra-program ./examples/sierra/zklend_fuzzing.json --entry-point zklend::fuzzing::Fuzzing::__wrapper__fuzz_scaled_down_amount --seed 1739662178
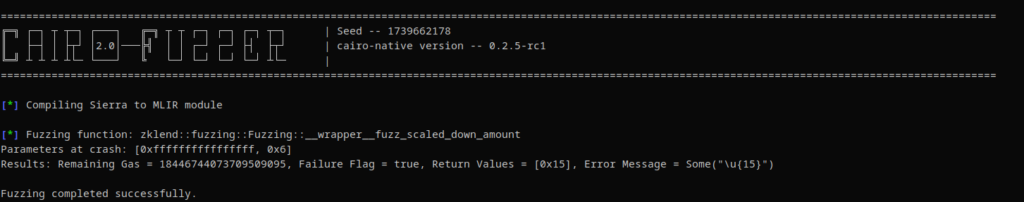
We also created a new detector on our analyzer to detect rounding errors

Tools Securing the StarkNet Ecosystem
In our ongoing work to secure the StarkNet ecosystem, we’ve built a set of tools that cover every base. Thoth is our go-to framework for scanning smart contracts for vulnerabilities. Meanwhile, Cairo-fuzzer automates fuzz testing to expose edge cases and subtle issues. On top of that, Sierra-analyzer inspects the compiled output to catch potential problems.
Together, these tools provide a proactive approach to security, reflecting our commitment to building a safer, more resilient smart contract ecosystem.
Lessons Learned
This incident underscores several important points:
- The Value of Fuzz Testing: Even a basic fuzzing harness can expose critical vulnerabilities. Automated fuzzing should be an integral part of the security testing process for smart contracts.
- Code Review and Invariants: Maintaining strict invariants (e.g., ensuring that scaling down does not increase values) is vital. In this case, a simple assert could have served as an early warning mechanism.
- Community Collaboration: By sharing our findings, we hope to inspire further community-led security reviews and foster a proactive approach in securing smart contract ecosystems.
Conclusion
The ZKLend hack serves as a cautionary tale about the importance of thorough testing and validation. By leveraging simple yet effective fuzzing techniques, vulnerabilities that might otherwise go unnoticed can be detected and mitigated early in the development cycle.
Patrick Ventuzelo / @Pat_Ventuzelo
Antonin Fagat / @Rog3rSm1th
Mohammed Benhelli/ @MohammedBenhelli
Nabih Benazzouz / @Raefko
About Us
Founded in 2021 and headquartered in Paris, FuzzingLabs is a cybersecurity startup specializing in vulnerability research, fuzzing, and blockchain security. We combine cutting-edge research with hands-on expertise to secure some of the most critical components in the blockchain ecosystem.
Contact us for an audit or long term partnership!